**Update: Featured image was updated to change Netflow collector instead of server 05/27/2020
Netflow is a network protocol that provides a look into the network traffic and the capability to monitor the flow of data traversing the network. Traditional Netflow and Flexible Netflow is a feature that was added to Cisco routers. Flexible Netflow is an extension of traditional Netflow. It provides an insight into network traffic as does Traditional but in addition, Flexible Netflow provides the ability to monitor a wide range of packet information and expansion of Traditional Netflow. This flexibility and additional specific data are useful to troubleshoot network problems.
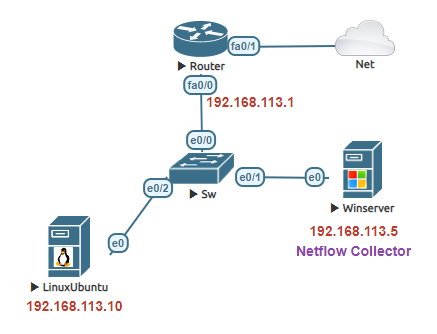
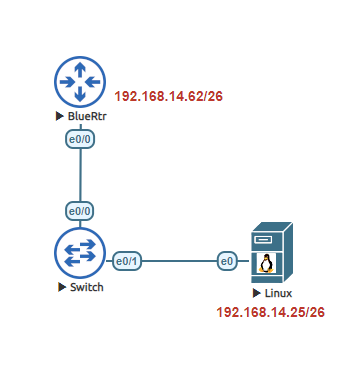
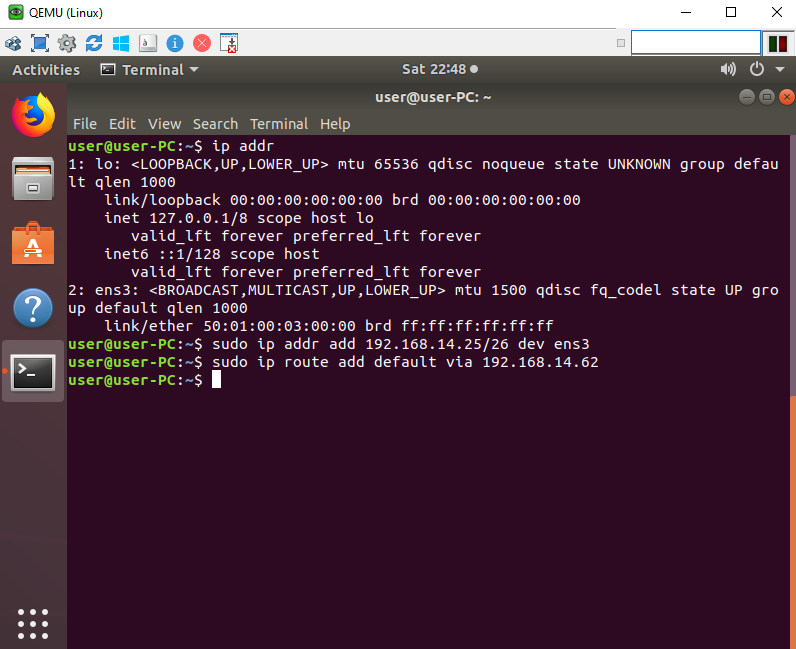
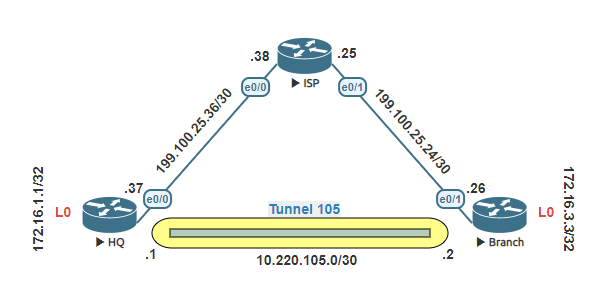
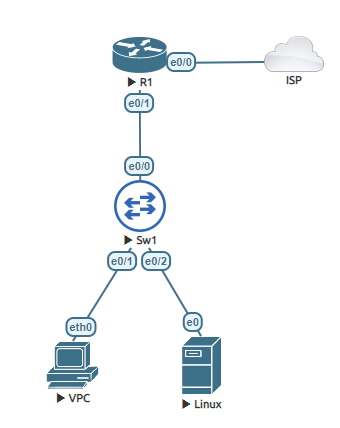
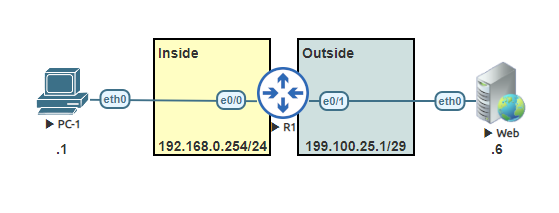
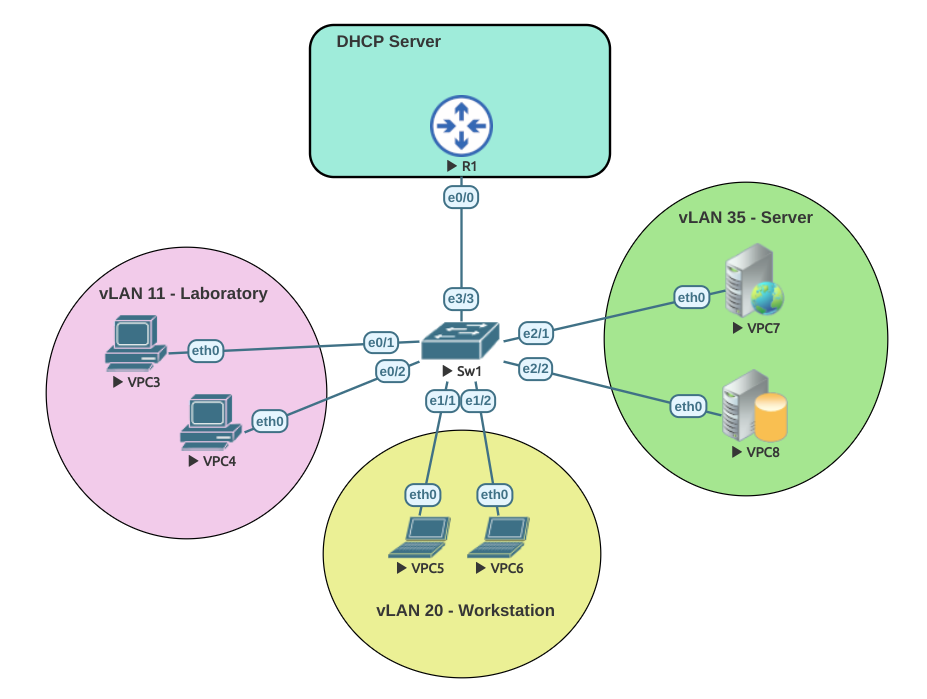
Before getting into those steps of each Netflow lets setup the router to use NAT overload.
Traditional Netflow
Step 1: Define the IP address of the Netflow collector and the UDP port to be used. In this example, we will use UDP 2055.
Step 2: Specify the version of Netflow the export will use. For this example use version 9.
Step 3: Enable Netflow on the interface that you wish to monitor the ingress and egress Netflow traffic.
Flexible Netflow
Step 1: Configure a flow record.
Step 2: Configure a flow exporter
Step 3: Configure a flow monitor
Step 4: Apply the flow monitor to an interface
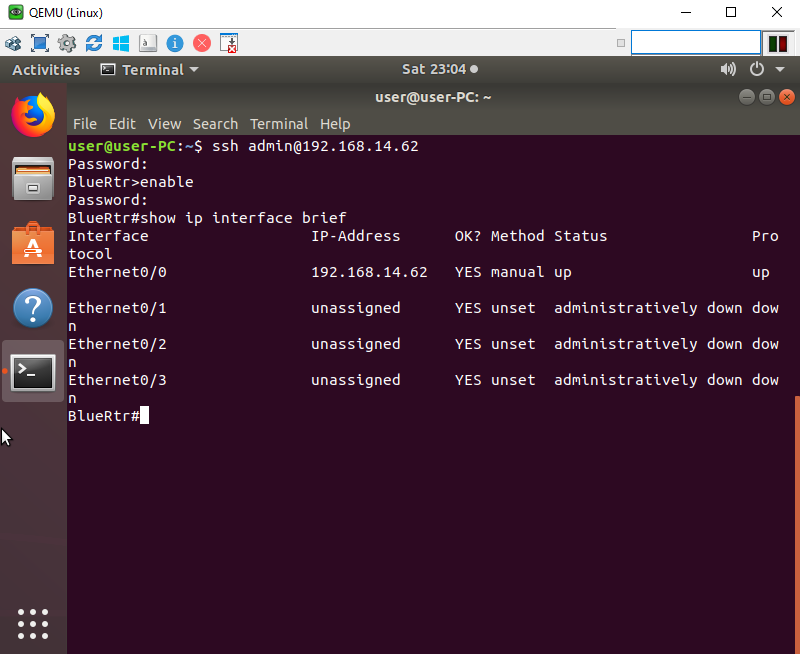
Verify the NetFlow flow monitor statistics to see if the Router is collecting from the interface identified.
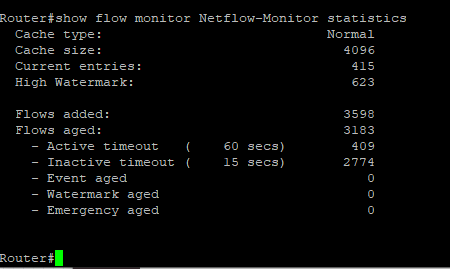
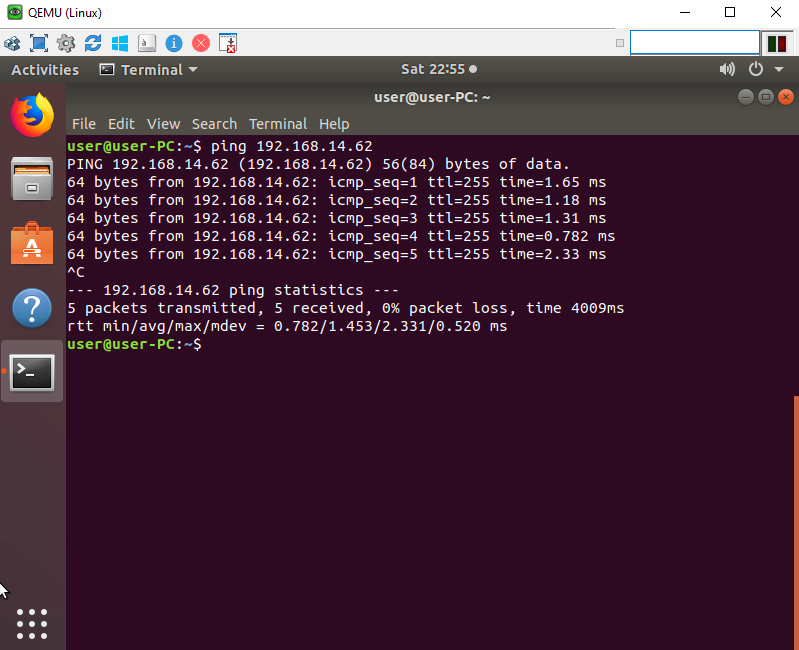
To test generate network traffic by browsing and/or pinging websites.
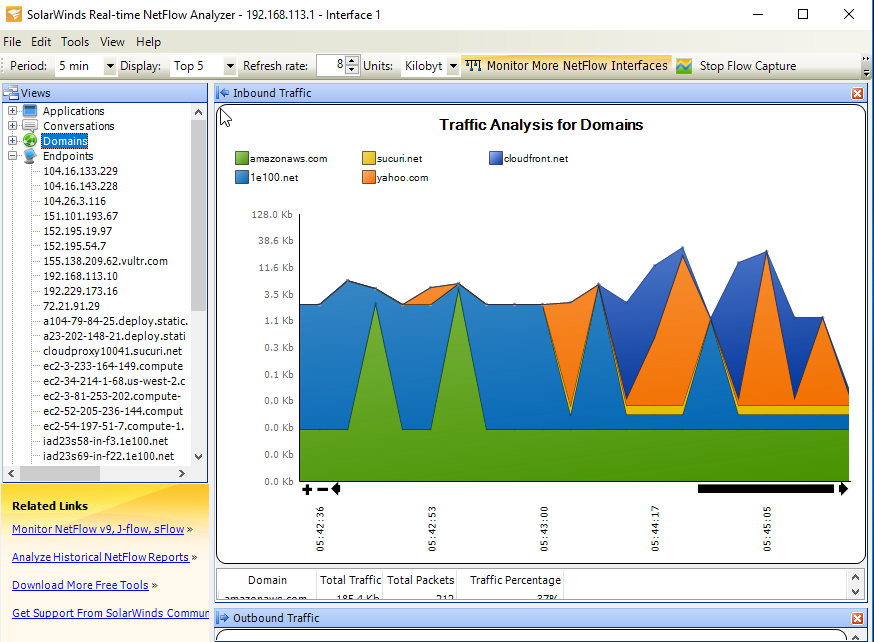
Verify the Netflow Collector is receiving the data. I used Solarwinds Real-Time Netflow Analyzer. It is free so long that you register a Solarwinds account. There are many open source programs as well that collect Netflow flows.