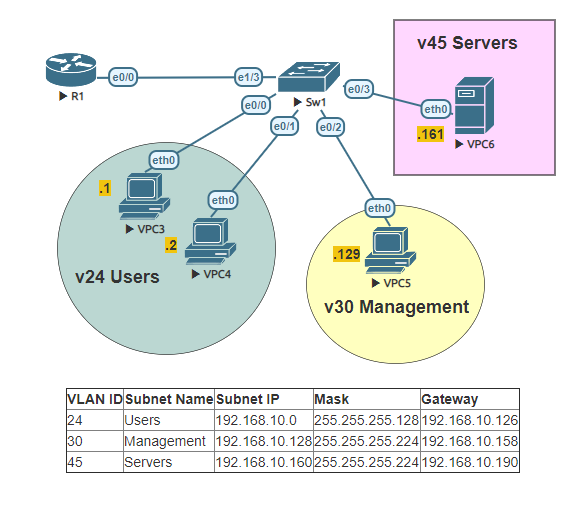
This is a basic lab, that will reinforce a common use of inter-VLAN routing. Most enterprise networks separate their traffic using VLANs. VLANs are virtual isolated LAN segments.
VLANs define the limits of broadcast domains in a Layer 2 network. A broadcast domain is typically bounded or enclosed by routers as they do not forward the broadcast frames. VLANs enforce a boundary, limited to the amount of devices on a particular subnet. In order to allow communication between the subnets a layer 3 device is needed, as traffic cannot pass directly to another VLAN.
Task 1:
Configure the hostname on both the router and switch.
Task 2:
Configure the subinterfaces using 802.1q encapsulationon the routers interface. Subinterfaces should match VLAN IDs. Assign IP addresses in each of the subinterfaces, using the identified gateway and subnet mask.
Task 3:
Verify the ports are up and operational and that they have the correct IP Address assigned on each subinterface.
Task 4:
Add VLANs to VLAN database on switch. Name them properly defined in the table next to the topology.
Task 5:
By default trunks allow all vlans. Configure the trunk on switch and prune VLANs allowed to match sub-interfaces.
Task 6:
Configure access ports to match the topology on the switch.
Task 7:
Verify the status of the switch ports.
Task 8:
Configure the Virtual PCs with proper IP addresses and ping their particular gateway in order to verify that everything was configured properly. In the example below only one PC is configured, repeat the process for each PC.
This Lab was conducted on Eve-NG. The image used was Cisco IOL. The images were obtained from Cisco VIRL. This lab can be carried out in Cisco packet tracer.