Route summarization is the method of summarizing routes of multiple networks/subnets to router neighbors routing table. Summarization provides advantages for example:
Saves memory – smaller routing tables reduces the memory requirements
Saves bandwidth – with less routes that need to be advertised, less data is traversed.
Saves CPU cycles – smaller routing tables means less packets need to be processed.
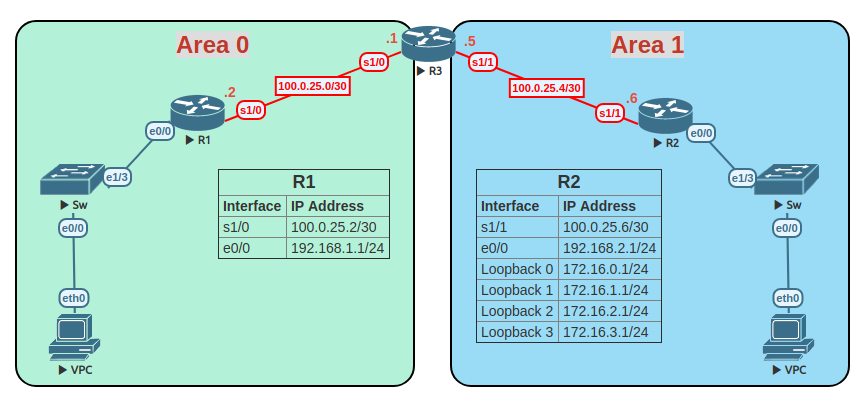
This is a multi-area OSPF lab, that provides an example of route summarization.
Task 1: Configure hostname of all three routers.
Task 2: Assign IP addresses to the physical interfaces on all three routers.
Task 3: Configure loopback addresses on Router 2.
Task 4: Configure OSPF on all three routers. Advertise the physical and loopback interfaces for each router. Identify each router’s id with the following:
R1 = 1.1.1.1
R2 = 2.2.2.2
R3 = 3.3.3.3
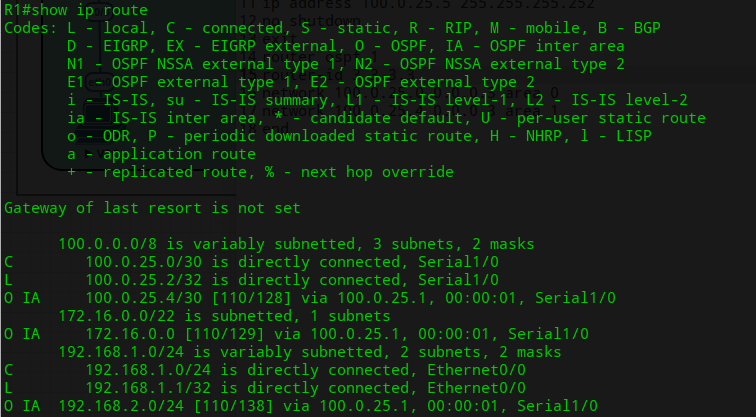
View the R1’s routing table after the OSPF process has been completed by all routers.
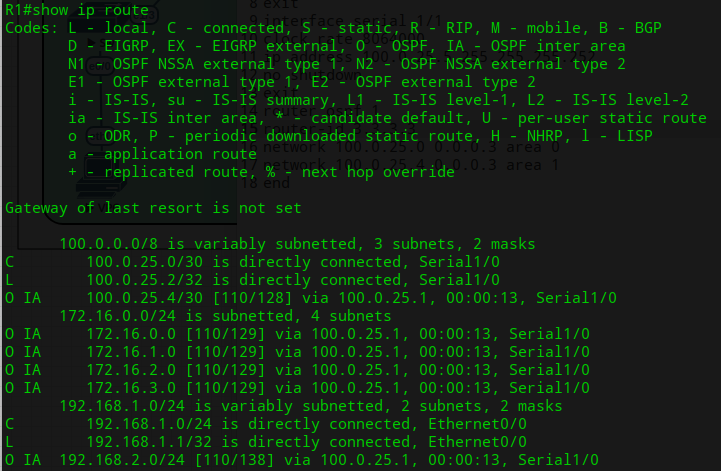
Task 5: Now let’s summarize what R3 shares to R1. Clear the OSPF process in order to force R3 neighbors to receive updates to the routing table learned from OSPF.
Finally, return back to router R1 and review the routing table, you will now see the routes summarized. The loopback interfaces routes should be seen as a single summarized route outside of area 1.