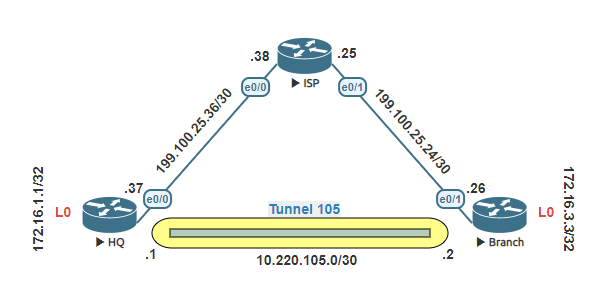
Generic Routing Encapsulation (GRE) is a tunneling protocol. This protocol allows the encapsulation of the network layer protocols inside other packets (packets into packets). Tunnel allows the expansion of a network that are separated in two different locations to create a point-to-point connection between the two sites.
In this lab, we will build a simple GRE Tunnel between two different sites. We are not going to encrypt the traffic, so therefore this is a non-secure remote location network.
Task 1:
Lets start with the ISP router. Configure the host name of the router and both interfaces.
Task 2:
Configure the HQ router. Configure the host name and both its public IP interface and the loopback 0 interface.
Task 3:
Configure the Branch router. Configure the host name and both its public IP interface and the loopback 0 interface.
Task 4:
In order for a tunnel to form. Both the HQ router and the Branch router will need to know how to reach each others public IP address. Add a static route on both routers to the others public ip. After both static routes have been implemented ping from the HQ router the Branch’s IP address.
Task 5:
Now we can create the tunnel interface in the HQ router. The tunnel source shall be the physical inteface towards the ISP. The destination will be the branch router public IP address.
Task 6:
Create the tunnel interface in the Branch router. The tunnel source shall be the physical port that connects to the ISP. The destination will be the HQ routers public IP address. Verify the connection after completion.
Task 7:
Now lets use a Dynamic routing protocol, in this lab I am going to use EIGRP. With the routing protocol configured we can have the HQ router and the Branch router learn about each other’s loopback address or in another instance the LANs IP address of the site. Verify after the configuration connectivity to the HQs Loopback from the Branch router.