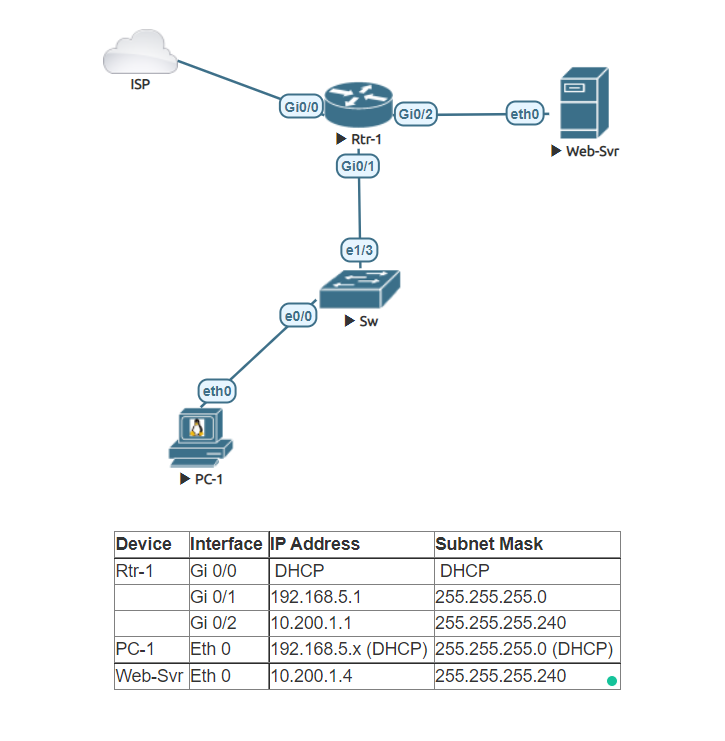
In this lab, we will run through the process of setting up a small network. We will use this network to show the different types of ACLs. We will start by using a standard named ACL in order to allow traffic to use NAT (PAT) to permit our workstation LAN network to access the internet. We will then create an extended network to permit web traffic but block others.
Change hostname Rtr-1
Access the router and change the hostname to ‘Rtr-1’. Configure the router to use Google’s DNS IP ‘8.8.8.8’.
Configure Rtr-1 Interfaces
Configure each interface of Rtr-1 as they appear in the table above.
Create a DHCP server on Router 1 name it Workstation-LAN
Setup a DHCP Pool named Workstation-LAN. Set the network as 192.168.5.0/24. Configure the DNS server to use Google’s DNS server IP address ‘8.8.8.8’. Set the gateway as the IP assigned to interface Gi 0/1. Reserve the first 25 IPs and the last 55 IPs.
Set up PC-1 to a Dynamic IP address
I am using a Docker container in this lab, but you can use a Linux VM, Windows VM, or even a Virtual PC. If you are using the Docker container in EVE-NG make sure to Enable DHCP on Eth 0 is checked in the configuration window.
Set up Web-Svr as a Static IP
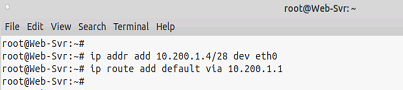
Configure the Web Server to use a static IP as it appears in the table above. Using a terminal configure the IP address. In this lab, I used a Docker container you can use a Linux VM, Windows VM, or a Virtual PC.
root@Web-Svr:~# ip addr add 10.200.1.4/28 dev eth0 root@Web-Svr:~# ip route add default via 10.200.1.1
Configure NAT Overload (PAT) on Rtr-1
Define the inside and outside interfaces on Rtr-1. Create a standard named ACL, using the name ‘NAT-ACL’. Permit the Workstation-LAN on the ACL. Set the ACL ‘NAT-ACL’ as the inside source and set the outside interface to overload.
Verify PC-1 can access internet websites
Open an RDP session to PC-1 and open a web browser and connect to any website to verify connectivity.
Start a simple web server
If you are using Docker Container in Eve-NG Pro ‘Gui-Server’ as I did you will not need to follow these instructions. If you are using a Linux VM add the following commands in the Linux terminal.
sudo apt update sudo apt install apache2
After entering those commands you should be able to open the PC-1 web browser and access the apache webserver by typing the Web-Svr IP in the search bar of the browser like so ‘http://10.200.1.4’.
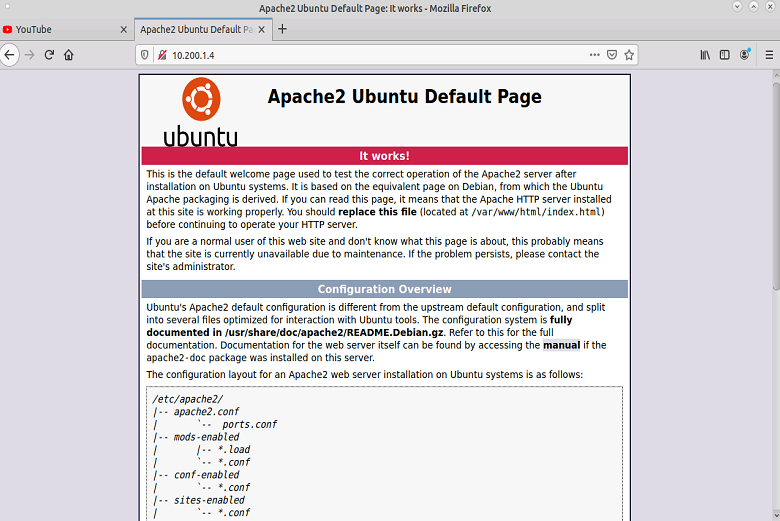
Start a Python SimpleHTTP Server on port 8080
Return back to the Web-Svr terminal and enter the following command in order to start an additional webserver on the Web-Svr.
root@Web-Svr:~# python -m SimpleHTTPServer 8080 Serving HTTP on 0.0.0.0 port 8080 ...
After entering those commands you should be able to open the PC-1 web browser and access the SimpleHTTPServer app using port 8080 and the IP address of the Web-Svr.
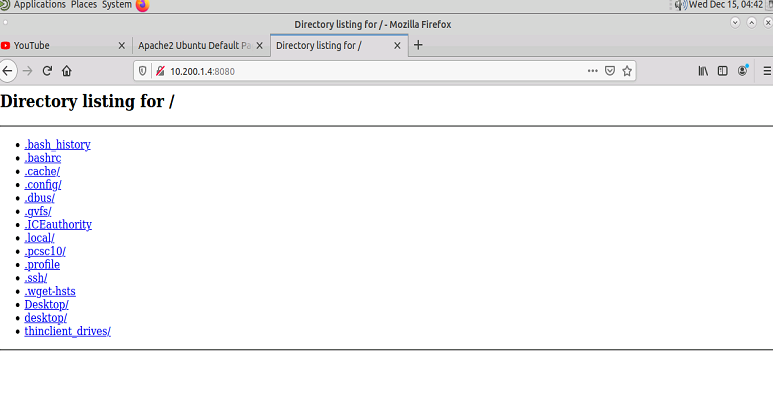
Create an extended ACL to block PC-1 access to port 80 but continue to permit 8080
Access Rtr-1 and configure an extended ACL using the access-list number 104. Assign the ACL to the appropriate interface. Remember the ACL created should be configured closer to the source.
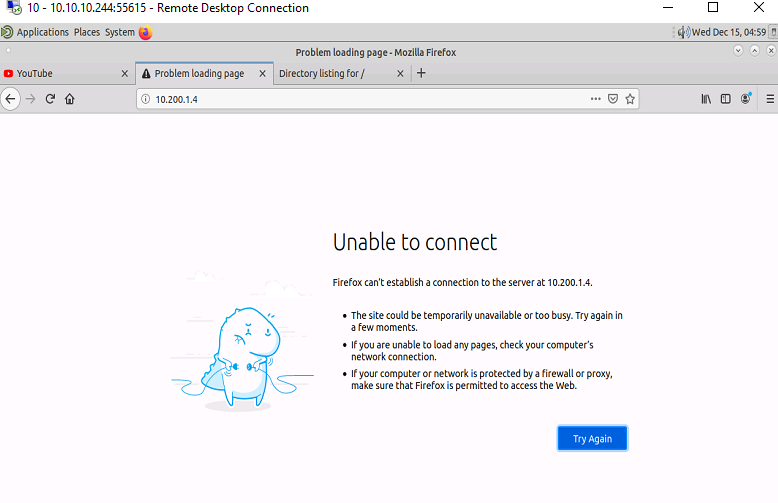
Verify that PC-1 no longer has access to Port 80 of the Web-Svr
Verify the PC-1 still has access to port 8080 of the Web-Svr
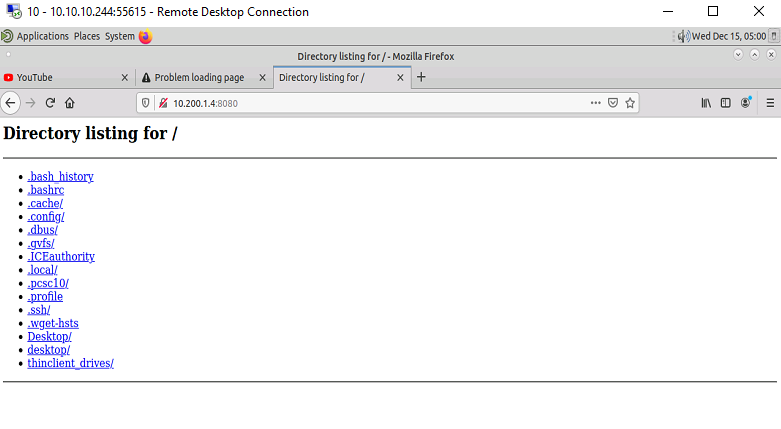
Uh oh PC-1 No longer has access to the internet.
Fix the ACL so that PC-1 regains Internet Access
Change the ACL to permit all other traffic before the implicit deny.
Verify that PC-1 can now access the internet after the ACL changes
You have completed the lab.